SPOTLIGHT ON SECURITY
Website Tips for More Successful E-Commerce… attend this free webinar and get insight into key enhancements you can make that will increase shopper satisfaction and retention. Reduce cart abandonment & increase your average order size! Register Now.


Richard Adhikari has written about high-tech for leading industry publications since the 1990s and wonders where it's all leading to. Will implanted RFI chips in humans be the Mark of the Beast? Will nanotech solve our coming food crisis? Does Sturgeon's Law still hold true?
Facebook Enlists Websense for Neighborhood Watch
Facebook is trying to get a better handle on
the security of its members through a deal with Websense, which will
soon warn Facebook users whether the links on friends' posts might put
their computers at risk. Meanwhile, boffins propose an alternative to
security certificates, and users of HTC Android phones get a security
scare.
Website Tips for More Successful E-Commerce… attend this free webinar and get insight into key enhancements you can make that will increase shopper satisfaction and retention. Reduce cart abandonment & increase your average order size! Register Now.
Facebook, long a darling of cybercriminals looking to lure in unsuspecting cybersocializers, has partnered with content security vendor Websense to help protect members from links that lead to malware and malicious sites.
That may prove good news to corporations, where many IT managers
consider employees' use of social media a security threat but where few
of them do much about it, a global survey by the Ponemon Institute has
found.
In other security news, experts are suggesting an alternative to the
security certificate, which cybercriminals have shown to be an imperfect
safeguard.
Meanwhile, it seems that many types of HTC smartphones running Android have a vulnerability that leaves users wide open to having their data stolen.
Security experts have been warning about the danger of a mobile
security tsunami since users began bringing in their own tablets and
smartphones for use in the enterprise. HTC's reportedly looking into the
issue.
Facebook's Doing It Better
Facebook has signed on Websense to protect the social networking site's
members from links that lead to malware and malicious sites.
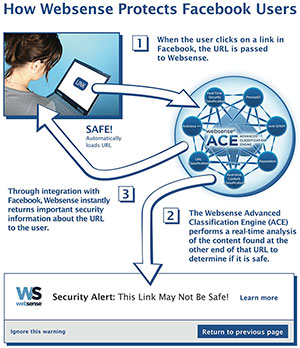
When a Facebook member clicks on a link, that link will be checked
against Websense's database. If that link's deemed to be malicious, the
system will return a page that contains various choices -- to continue
at the member's own risk, return to the previous screen, or get more
information.
That level of security may prove useful to enterprises. A survey of
more than 4,000 IT and IT security practitioners in 12 countries by the Ponemon Institute found 63 percent believe employees' use of social media in the workplace constitutes a serious security risk.

Further, 52 percent of the respondents experienced an increase in malware attacks because of employees' use of social media.
However, only 29 percent of the respondents reported having the necessary security controls in place to deal with that risk.
That lag between implementing security controls and the level of
security issues experienced by the respondents is due to the rapid
increase in the use of Facebook, said Tom Clare, senior director of
product marketing at Websense.
Systemic issues constitute other reasons for the lag.
IT buys in multi-year cycles for technologies including security, "so
any innovations or disruptive growth areas between cycles become an
area of concern," Clare told TechNewsWorld.
"Also, as new areas like social media quickly evolve, the risk impact
becomes visible, and security measures are frequently applied
afterwards," Clare said.
A Cert's Just a Bunch of Electrons
Digital certificates have been used for years by the security-minded, but recent events, including the DigiNotar issue, have led some in the cybersecurity field to consider alternatives.
Security expert Moxie Marlinspike, for one, launched the Convergence Project at the Black Hat cybersecurity conference in August.
This offers a browser-add-on to replace the existing certificate authority infrastructure in a browser.
Normal browsers work by including trusted certificate authorities who
have been listed by the browser vendors. When you go to a site
protected by a digital certificate, the browser checks that certificate
against the preapproved certificate authority that issued it.
However, certificates can be spoofed or stolen. For example, hackers
recently broke into Dutch CA DigiNotar's network and stole and issued
rogue certificates.
"The system in its current shape suffers from two major weaknesses,"
Ivan Ristic, director of engineering at Qualys, told TechNewsWorld.
"One is that any CA can sign any website, which means that a
compromise of one CA will compromise the entire system," Ristic
continued. "The other major weakness is that it's too easy for those
with resources to perform stealth interceptions of someone else's
encrypted traffic."
In the notary system, whenever you visit an SSL
site, your browser talks to two or more remote parties, called
"notaries," and asks them whether they see the same certificate it does.
If the answer's yes, your browser trusts the site.
The key advantage of Convergence is that the user can decide whom to trust.
"The extremely paranoid can even build their own notaries," Ristic pointed out.
The notary system will help deter man-in-the-middle attacks where a
third party illicitly intercepts communications between two parties.
However, he admits that many questions still remain to be resolved.
Insecurity on the Go
The latest manifestation of mobile technologies security issues comes in
the form of a problem HTC smartphones running Android are facing.
Expect more mobile security problems down the road.
IBM's (NYSE: IBM) X-Force 2011 predicts that the number of exploits will double this year.
"That statistic is specifically about exploits for mobile devices,"
Leslie Horacek, X-Force threat response manager, told TechNewsWorld.
An exploit is a script or piece of code that takes advantage of a
vulnerability in an application, operating system or a service, Horacek
said.

Richard Adhikari has written about high-tech for leading industry publications since the 1990s and wonders where it's all leading to. Will implanted RFI chips in humans be the Mark of the Beast? Will nanotech solve our coming food crisis? Does Sturgeon's Law still hold true?

No comments:
Post a Comment